ClevGuard Support: Monitor Devices with Others' Permission.
Nowadays, mobile phone is an indispensable part of human life. In this digital age, many lawless elements are trying to obtain other people's information by high-tech means. The attackers can easily access people's mobile phone.
Are you wondering who hacked your phone? Are your bosom friends, your beloved spouse or someone else? If you want to learn how to trace a phone hacker, just keep reading and you will the answer you want.
- Part 1. How to Know If Your Phone is Hacked?
- Part 2. How to Find Out Who Hack Your Phone?
- Part 3. How to Avoid Attacks from Hacker
- Conclusion
How to Know If Your Phone is Hacked?
Your mobile phone might display or show some suspicious or inappropriate behaviors on your phone, but you are not 100% sure if your phone is hacked. Don't worry, here we have listed some methods and signs that you can effectively check if your phone is hacked or not.
Verify if Your Phone is Hacked with ClevGuard
At first, we recommend that you use one third-party app named ClevGuard to check if your phone is hacked or not. ClevGuard is an anti-spyware tool that can protect mobile phone data security. It can help you find if there are hidden spy apps on your phone, and remove risks in your phone. ClevGuard would be your best choice.
How to Know if Your Phone is Hacked with ClevGuard
With ClevGuard's help, you can find out if your phone is hacked or not in a few minutes, let's see these 3 easy steps below:
Step 1: Download and Install ClevGuard Phone Anti-Spy App
Press "Get it on Google Play" below and download ClevGuard after skipping to the download page. It will only take 1-2 minutes to finish the installation process.
Step 2: Check if There is Malicious Softwares On Your Phone
Open ClevGuard App and click on the "Scan" button to check if there are spy apps on your phone. ClevGuard is a powerful phone hacker scanner for scanning your phone, detecting, and cleaning all spy apps.
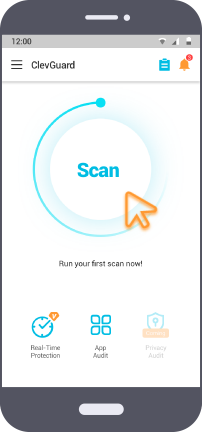
Step 3: Vertify if Your Phone is Hacked
Check the Scanning result, you will confirm if there are spy apps on your phone. If there are spy apps on your phone, you can choose "Fix" to remove spy apps readically in a few seconds.
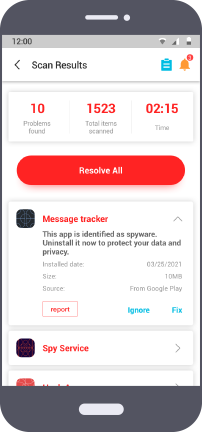
Other Signs of Phone is Hacked
Here, we also list some common signs of a phone is hacked for you to take them as a reference, but it cannot be 100% confirmed. Therefore, we recommend that you use ClevGuard to get the confirmed result.
- Cell Phone Decreases Charging: Malware apps use more power that's the reason decrease in Power. There may be malware running in the background so you may notice the phone doesn't perform fast. When your phone is hacked you can see many unusual new logins.
- Phone Spam Pop-ups Arise: Sometimes your phone screen appears in pop-up windows asking the user to perform various actions. Most people would never know their phone has been hacked until they have charges to their bank account or new lines of credit opened in their name. This is because a hacker will run a script to scan the phone for user data and collect it without evidence.
- Heard Phone Background Noise: If you can observe your calls dropped, the inability to make calls at times when you appear to have good signal strength, strange noises occurring during your phone conversations, then your phone is hacked. It is imperative to find out how to remove a hacker from my phone.
- Mobile Phone Data Increases: Has my phone been hacked? If you have monitored your phone data and SMS usage and see greater use than expected, maybe a sign that malware is transmitting data from one device to another device. If you can check your Phone data usage is greater - it is using way too much data for the functionality that it provides.
- Sending Strange Text Messages By Your Phone: If your friends report receiving messages that you didn't send, and you don't know anything so your phone is hacked. If you can see strange text messages coming from another unknown so you have understood your phone is hacked.

How to Find Out Who Hack Your Phone?
The most common mobile phone hacker is spyware. It can be dangerous for survivors because it can monitor many things you do on your smartphone, including photos and videos, and the short messages you send and receive.
Before tracing a mobile phone hacker, the problem is how to find out who hacked your mobile phone? IP addresses can be used to identify the attacker. However, only professional technicians can do it. The only thing we can do is to find the spyware on our mobile phone and delete it to protect your privacy.
Spyware that allows another person to secretly monitors and record information about your phone activity. Mobile spy tools, especially the tools on smartphones such as Android, iPhone, Blackberry and Windows phone, are widely be used in this generation. There are several reasons for using these tools, such as wanting to know someone's current location, telephone record or calls, monitoring social media accounts, etc. Except for parental monitoring and employee monitoring, other monitored behaviors are completely illegal. Therefore, more importantly, we must find a way to remove hackers from phone.
How to Avoid Attacks From Hacker?
If you want to be proactive, there are several tips you can take to protect yourself avoid attacks from hackers. Let's check them out.
Run ClevGuard Real-Time Protection: As a powerful anti-spyware tool, ClevGuard provides 24/7 real-time protection for phones. If you have installed ClevGuard on your phone, it will protect your phone at any time and anywhere. If there is any dangerous issue, it will notice you right away, which can help you effectively avoid hacking attacks.
Change Your Passwords: If your password is not strong so you can change it. Password is a combination of letters, digits, and special symbols. 91% of people are using the same password. Your passwords of software accounts, social media accounts, should be Strong and unique.
Do A Factory Reset: For your android device, simply go to the settings, then the system advances after which you should go to the reset option and erase all data. This is one of the useful steps to erase harmful files and avoid the attack.

Keep Applications Up-to-date: In addition to potential faster load times, outdated applications can crash and hack easily. If you have updated the Application, so it means you have to protect your personal information.
Keep Your Smartphone with You All the Times: If you have to keep your phone with you, a hacker will have to work much harder to access your information. Physical Access is an easy way to hack your phone.
Don't Jailbreak Or Root Your Phone: Root and jailbreak are almost the same things. Both adding methods ultimately remove restrictions that Apple and Google put in place, and both achieve this by giving you access to the protected files in your operating system. So don't use jailbreak or root your phone.
Enable Two-Factor Authentication(2FA): Multi-factor authentication can give you protection. Apple ID and Google accounts offer 2FA in case your device is used by unpleasant actors, so always activate it for more security. But in most cases, the extra authentication is simply a numeric code and digits.
Conclusion
Phone hacks are very common issues. Through the above contents we discuss when our phone does not work properly like pops up, background noise, these are the signs of your phone has been hacked. You need to find a better solution to solve problems if you suffer these conditions. There exits potential dangerous will bring chaos to our life because we use our cell phone every day. How to remove a hacker from my phone? Just following the methods that article provide, detecting malicious software on your phone and remove it. ClevGuard is your priority choice since it has excellent features to offer you 24 hours protection by scan all files on your phone and let you divide them into whitelist or blacklist at ease.







