ClevGuard Support: Monitor Devices with Others' Permission.
There could be cases for you to search for command-prompt hacking. Maybe you're a boss, you've found that the company's confidential documents have been leaked, and you want to check the employee's computer to see if someone has stolen the company's documents. Or you want to check your children's computers for parenting purposes. In this article, you will find out how to hack a computer with a command prompt and do command hacks.
What Are CMD Commands for Hacking?
CMD (Command Prompt) is a command-line interpreter in Windows operating systems that allows users to execute text-based commands to perform various tasks. CMD commands are used for system management, troubleshooting, and configuration, among other functions.
It automates tasks via various scripts and batch files, performs administrative functions, and solves many issues that become trouble for the user. Moreover, it is used to issue various commands to a system, like file management commands such as copy and delete, etc.Sometimes it is referred to as a command shell or CMD prompt, or even by its files.
How to Hack Using CMD Prompts
How do you remotely access another computer using a command prompt?? Before you know how to take advantage of CMD commands for hacking, you have to enable this particular feature on the target's computer.
Phase 1. Set up the remote desktop beforehand
To do this, you need a business or pro version of Windows operating system. Pay attention to approaching the target's computer first, including access to their computer's account and password, if you choose this method to use. Here are the steps to set up a remote desktop on someone's computer.
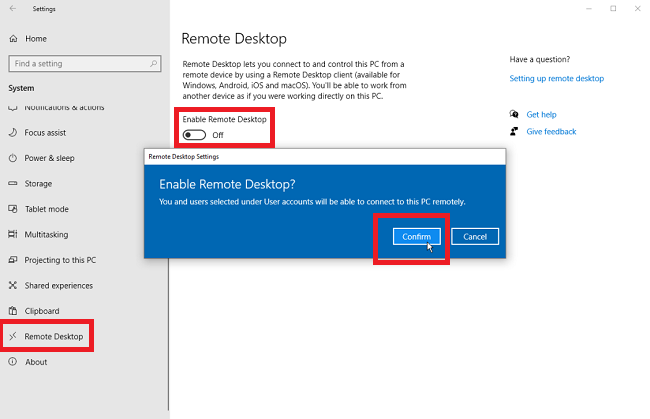
Step 1: From the Windows button, go to the Start menu.
Step 2: Click on the gear icon, which symbolizes the Settings.

Step 3: Click on System and then on Remote Desktop.
Step 4: Switch on Enable Remote Desktop.
If you are using the older version of Windows, you need to follow the steps given below.
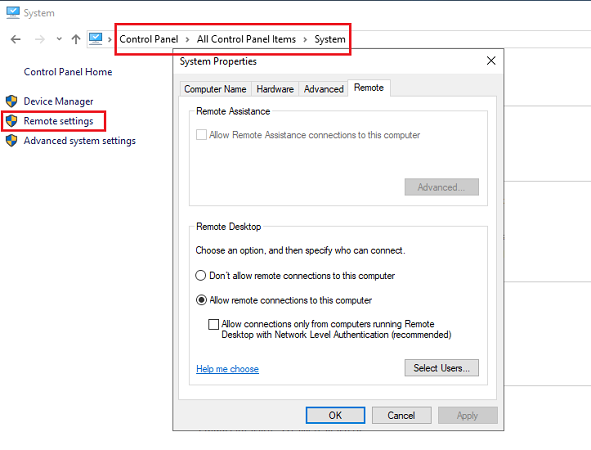
Step 1: From Control Panel, go to System and Security.
Step 2: Click on Allow Remote Access under System.
Step 3: From the Remote tab, select the radio button present near Allow remote connections to this computer.
You can use either of these two methods to set up remote desktop connections on your computer system. The method depends on the Windows version installed in the system. Then you go to phase 2 and start hacking a computer using the command prompt.
Phase 2. How to hack another computer with CMD prompts
Once you have followed the above steps, you can hack using CMD prompts to remotely control another computer and access their computer system. Here are the steps to know how to remotely access another computer without permissions and using CMDs.
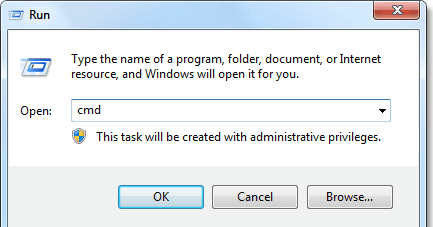
Step 1: Press Windows and R key together.

Step 2: Key in cmd and hit Enter.
Step 3: Key in mstsc to launch remote desktop connection app.
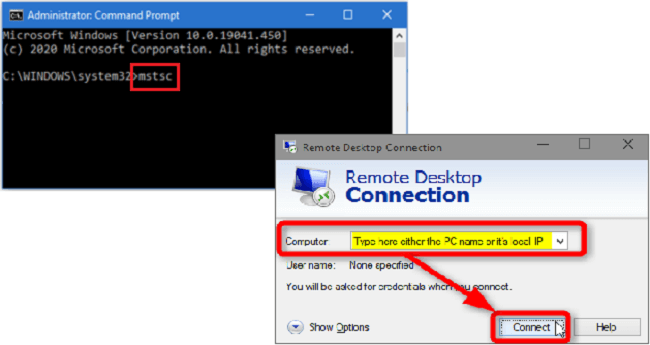
You can also directly access the computer by using additional terms as follows: mstsc/console/v:computername. This will take you directly to the login page of the target's computer.
Instead of "computer name", you can even key in your computer system's public IP address.If you do not know the IP address of the target's computer, you can search for "What's my IP" on Google through the target's browser.
Limitations of Using CMD Commands for Hacking
There are certain limitations to hack using CMD prompts. Some of them are listed below.
1. If the target's computer has not earlier configured a remote desktop computer system, you cannot hack into the system using this method.
2. For this method to work, the target's computer needs to be on and not in sleep or hibernation mode.
3. This method of hacking into others' computer systems fails if you do not remember the name and account of the target's computer.

It's important to clarify that using CMD commands for unauthorized access to systems, or "hacking," is illegal and unethical. Hacking without permission is a crime and can lead to severe consequences, including legal action, fines, and imprisonment.
MoniVisor: How to Remotely Access Another Computer
Now you have figured out it's not an easy job to hack using CMD prompts, right? Here's another effective way to track someone's computer activity - MoniVisor.
It is a highly recommended employee monitoring tool that enables seamless monitoring of all activities and access to any files stored on the target computer. The software only requires one-time physical access to the target device for installation. Rest assured, the program operates in stealth mode, remaining completely undetectable during use.
How to use MoniVisor to access another computer secretly
Step 1: Click the Try It Now button below to choose a plan and get a valid MoniVisor account using your email ID.
Step 2: Follow the instructions and configure your computer settings accordingly.You need to install an extension on the browser if you want to monitor the target's social media and email.
Once you complete the configuration, the app will be hidden, and the data on the target's computer will be updated automatically.
Step 3: Log in using your credentials to the online dashboard from any other device to view all the activities.
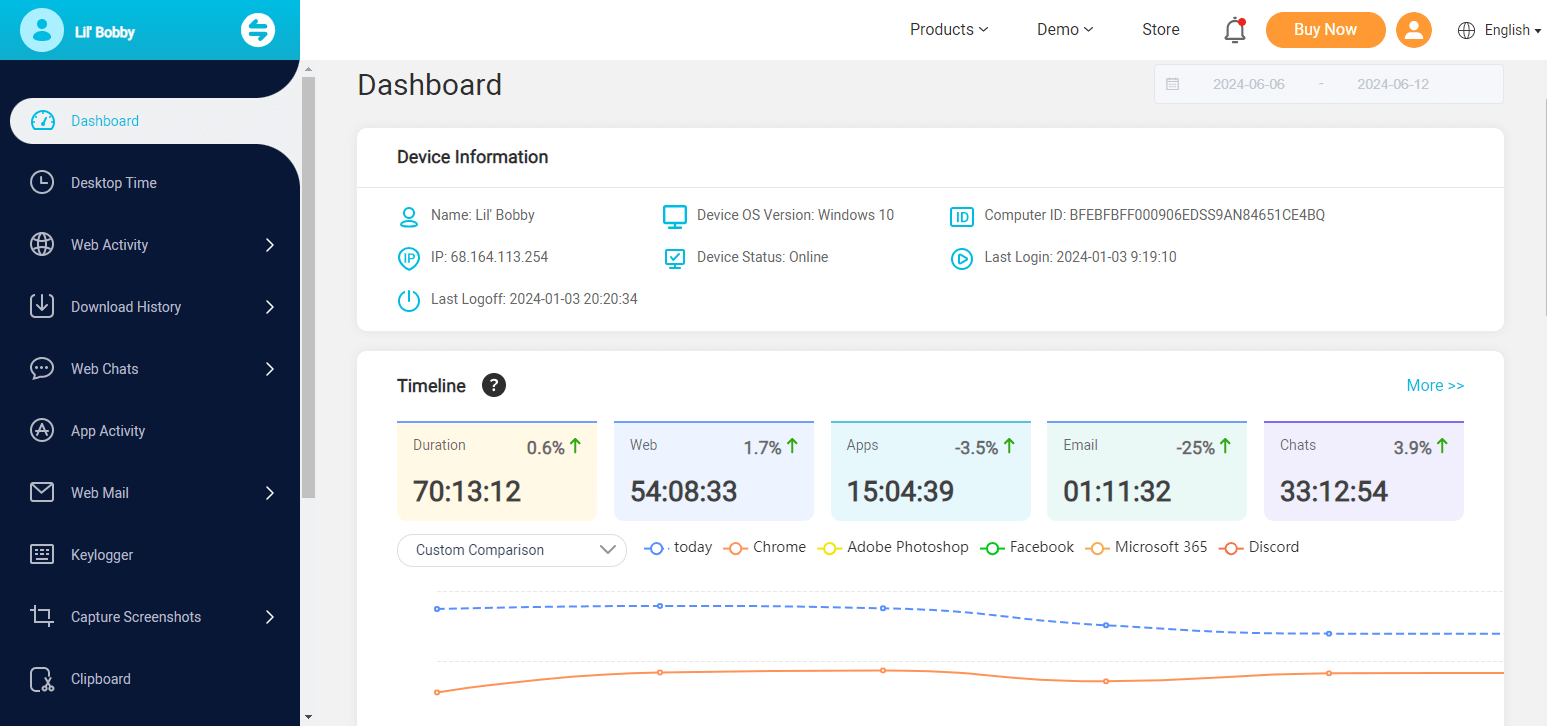
Features of MoniVisor
-
Monitor online communication, such as Whatsapp, Facebook (Messenger), Twitter, Skype.
-
Track someone's internet activity and the download history in Chrome, Firefox, Edge, and Opera.
-
Keep tabs on the email exchanges, including the content and contact information.
-
Take screenshots and record the computer screen automatically and silently.
-
Monitor keystroke inputs including the deleted chat history.
-
Track software usage to know the last active of a specific app.
-
Monitor Windows login activity to detect any unauthroized access.
Why MoniVisor Is Ideal for Computer Monitoring, Not Command Prompts
There are numerous advantages to using MoniVisor, a preferred option for remote computer monitoring, especially when it comes to monitoring another computers without someone's knowledge.
- MoniVisor offers an intuitive and user-friendly interface, making it accessible even to those without extensive technical expertise. This is far more straightforward than the command-line environment of CMD, which requires specific commands and knowledge to navigate.
- MoniVisor is designed specifically for comprehensive computer monitoring, such as real-time monitoring, data export, and activity tracking.
- Command prompts for hacking require technical skills while MoniVsior doesn't. You just need to install the software on the target device and then monitor from the online dashboard.
- MoniVisor operates in stealth mode, ensuring that the monitoring software remains undetectable by the user of the target computer.
Summary
To sum up, we have already figured out how to hack using CMD prompts. However, since the hacking is not legal, we offer another choice to remotely monitor someone's computer - MoniVisor. This is absolutely one of the most reliable computer monitoring programs you can try in 2024. A wide array of useful features, affordable pricing plans, along with simplified installation make it your go-to option regarding PC monitoring. Go check the Free Demo below to take a closer look for yourself.







