ClevGuard Support: Monitor Devices with Others' Permission.
Hacking into someone's computer is not an easy task, especially with their IP address. It is possible, but really difficult. But this doesn't mean that what you are asking cannot be done. There are easy ways, for instance using CMD hack, and they don't require any technical knowledge. Now, let's learn how to hack an IP address of someone's Windows computer. Check out the article below.
Is It Possible to Hack an IP Address?
It is a difficult task, as there are thousands of ports for every IP address. If someone knows your IP address, then they will be able to connect to your computer directly. But a skilled hacker will use brute-force to access one’s computer remotely. So, how do you hack another computer using an IP address? It is discussed in the part below.
What Is IP Address Hacking?
IP address hacking refers to the unauthorized access, exploitation, or misuse of a device or network by targeting its IP (Internet Protocol) address. An IP address is a unique identifier assigned to a device connected to a network, allowing it to communicate with other devices on the internet. When a hacker obtains someone's IP address, they can potentially exploit it for various malicious activities.
How does IP address hacking work?
Identifying the IP Address: Hackers can obtain a user's IP address through various methods, such as phishing, online interactions (like chat or gaming), or simply by observing unprotected networks.
Scanning for vulnerabilities: Once the hacker has the IP address, they may scan the network or device for security vulnerabilities, such as open ports or outdated software, that they can exploit.
Gaining unauthorized access: If the hacker finds a vulnerability, they may attempt to gain unauthorized access to the device or network. This can include activities like:
- Denial-of-Service (DoS) attacks: Overloading the target’s IP with excessive traffic, causing the device or network to crash or become unusable.
- Remote control: Exploiting vulnerabilities to control the device, potentially stealing personal information, accessing sensitive files, or spreading malware.
- Spying: Monitoring internet activity, intercepting communications, or tracking online behavior. Masking Their Identity: Hackers often use techniques to hide their identity, making it difficult for the target to trace the source of the attack.
What You Can Do with Someone’s IP
Knowing someone's IP address can potentially reveal their approximate location and internet service provider (ISP). If someone obtains your IP address, they could potentially:
Geolocation: Determine your approximate location, such as your city or region. This is based on databases that map IP addresses to geographic locations.
Network diagnostics: Use it for network troubleshooting or diagnostics, like identifying connectivity issues or configuring network settings.
Potential security risks: In some cases, malicious actors might attempt to use your IP address for nefarious purposes, such as launching attacks or attempting unauthorized access to your devices or network. This is why it's important to have strong network security measures in place.
Tracking online activity: In certain contexts, an IP address can be linked to your online activities, such as which websites you visit. However, this typically requires additional data and is subject to privacy regulations in many jurisdictions.
How to Hack Someone With IP
Different procedures are available, but we will be discussing one that uses the IP address, and Command Prompt to hack into someone's computer. We should tell you that this method needs you to get the target's IP first, and then you should apply a third-party tool to scan the ports to hack someone’s computer eventually. Now, check out the steps below.
Step 1: Open Command Prompt and type the “net view” command. Or you can also use the “NB scanner” option in “IP Tools” software by entering the range of the IP address. By using this method, you can scan a number of computers at a time.
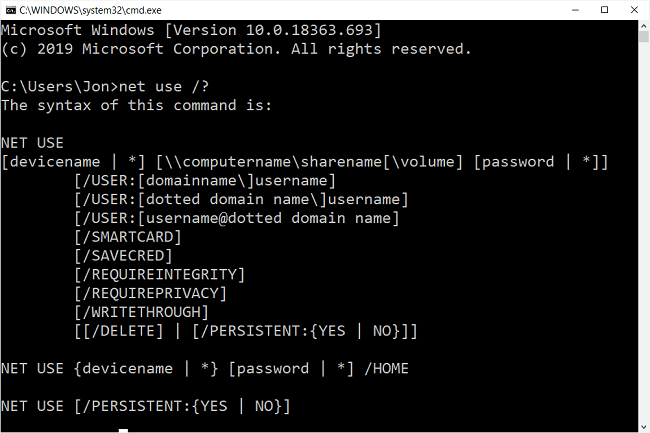
Step 2: Then, use the "Net Use" command in the command prompt. The "Net Use" is another netbios command that makes it possible to hack remote drives or printers.
Step 3: After this, the computer will pop up a message that "The command completed successfully". Once you get the above message, you are only one step away from hacking the computer.
Step 4: Now open "My Computer" and you will see a new "Hard-Disk drive" (Shared) with the specified name. You can open it and access the remote computer's hard drive. You can copy files, music, folders, etc. from the victim's hard-drive. You can delete/modify data on the victim's hard drive only if WRITE-ACCESS is enabled on the victim's system. You can access files/folders quickly through "Command Prompt".
IP Address Hacking - Ilegal or Not?
Hacking is illegal. It's a serious crime that can have severe consequences. Even if you only use an IP address to gain unauthorized access to a computer system, it's still considered hacking.
Why is hacking illegal?
- Privacy violation: Hacking violates a person's right to privacy. It's like breaking into someone's home without permission.
- Data theft and damage: Hackers can steal personal information, financial data, or intellectual property. They may also cause damage to the system or disrupt its operations.
- Cybercrime: Hacking is often associated with cybercrime, such as identity theft, ransomware attacks, and malware distribution.
Hacking is not only unethical but also illegal. It can lead to legal trouble and have a negative impact on your life.
How to Monitor Someone's Computer Secretly with MoniVisor
Though hacking a computer via the IP address is possible, there are however several preconditions and limitations. What's the most important, hacking IP address of someone's computer is illegal and definitively not recommended.
If you need to monitor someone’s computer remotely, we recommend ClevGuard’s MoniVisor - a computer monitoring program for Windows and macOS. It is the safest and most reliable option available on the market. Operation is simple, and installation is easy as well.
It works well on different Windows computers, and the online dashboard is intuitive, so it is easy to track someone's computer activities without an IP address. The use of it doesn't require any technical skills, and you can finish the software configuration within 5 minutes.
MoniVisor: How to remotely monitor a computer without an IP address
We have already stated that the installation and operation of MoniVisor are simple. But having a guide will be convenient and very helpful if you have decided to use this tool. So, check out the user-friendly guide below.
Step 1: Register for an account and then choose a plan according to your needs to enjoy all the features.
Step 2: After making the purchase, you can follow the on-screen instructions to install and activate the software correctly.
Step 3: Complete the activation on the target device. MoniVisor will start working in the background of the target computer without being detected. Visit the ClevGuard website and login to your account on your own computer; then you will get to the “Dashboard” option, and all the recorded data will be visible to you.
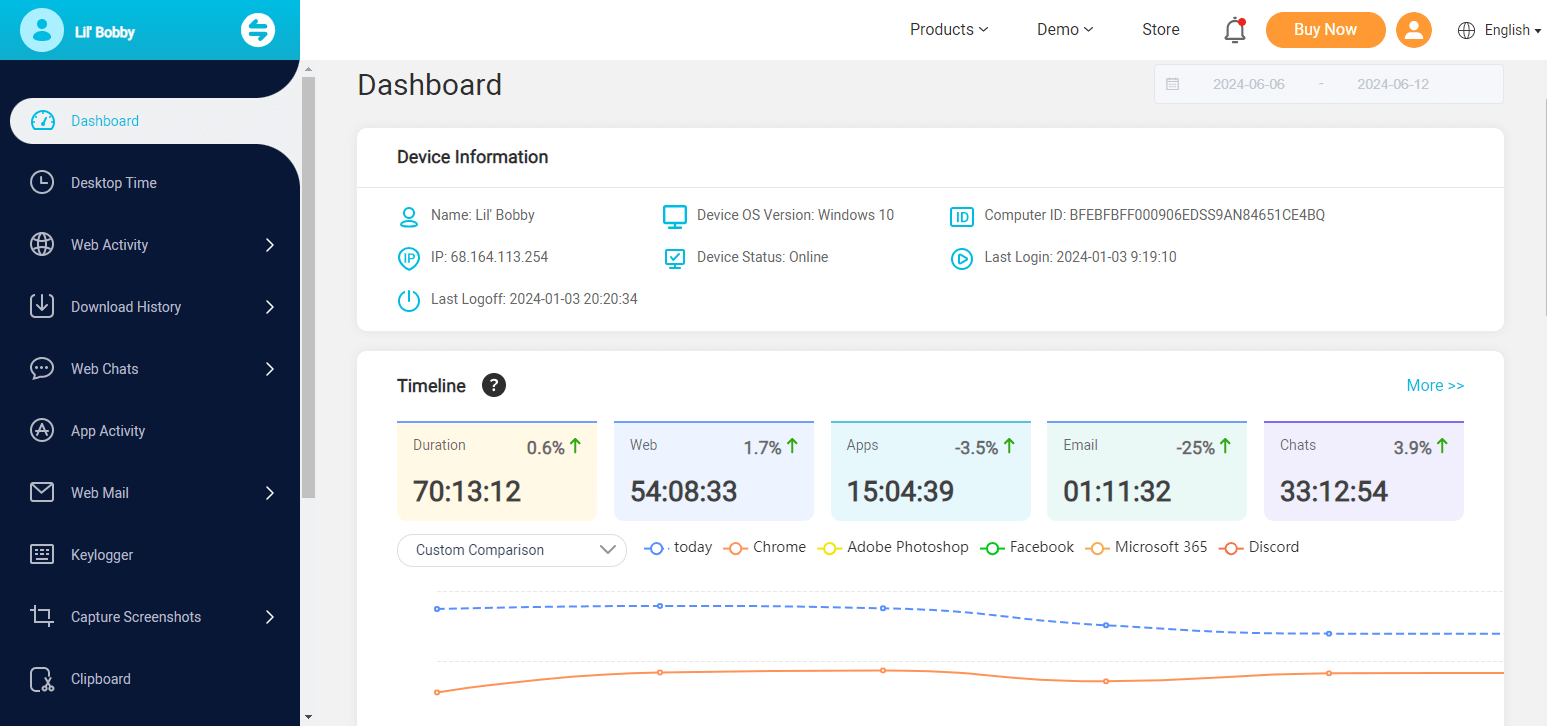
This is the easiest way to hack into any computer. Any kind of technical knowledge is not required, but you need to access the target device once to install the app.
What can MoniVisor do to monitor computer
MoniVisor is an excellent app, and it is equipped with unprecedented numbers of features for monitoring.
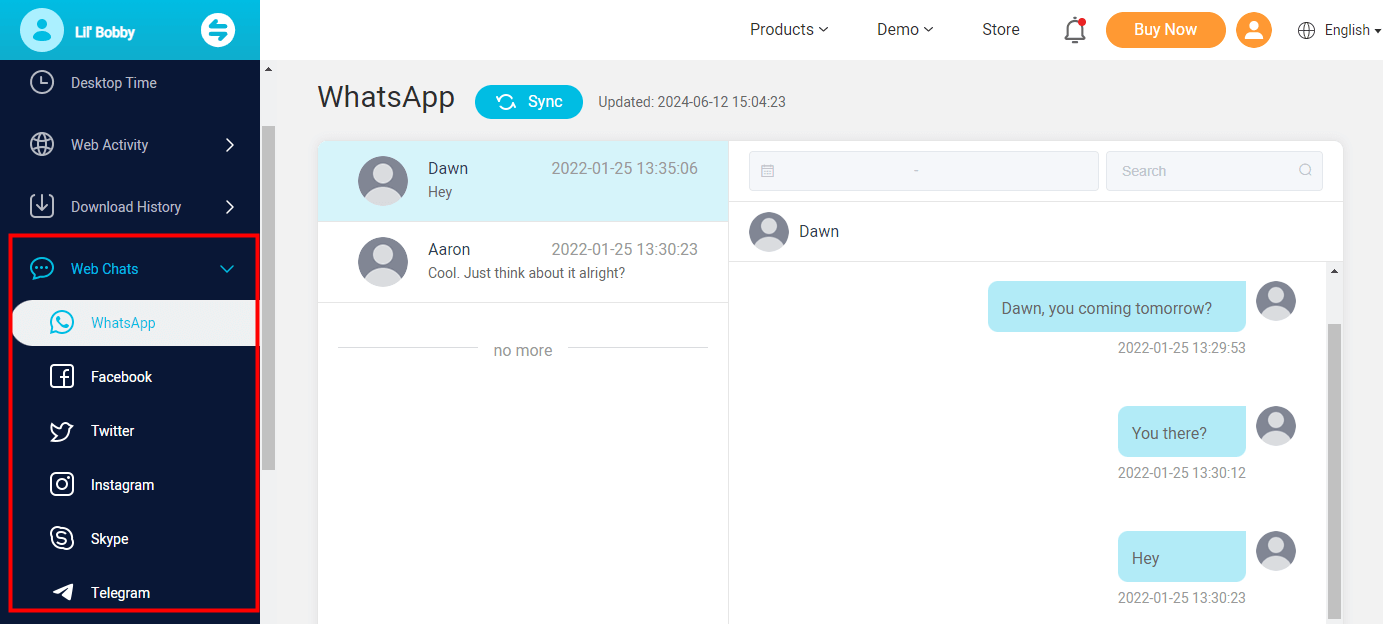
Record conversations on social apps
Conversations on Telegram, Facebook, WhatsApp, Twitter, Instagram, and Skype can be viewed. It can log all the chats and media files without logging into their account, and will also not be detected by the target user. You can view all the monitored data on your end.
Internet activity tracking
MoniVisor is a robust browser history monitoring program on computers. All internet activity on the browser will be tracked. That means all the browsing history and the download history on the target computer can be tracked and recorded, you can even directly click on the monitored URL to check what the target viewed. Amazing! It's 100% compatible with Opera, Internet Explore, Firefox, Microsoft Edge, and Chrome.
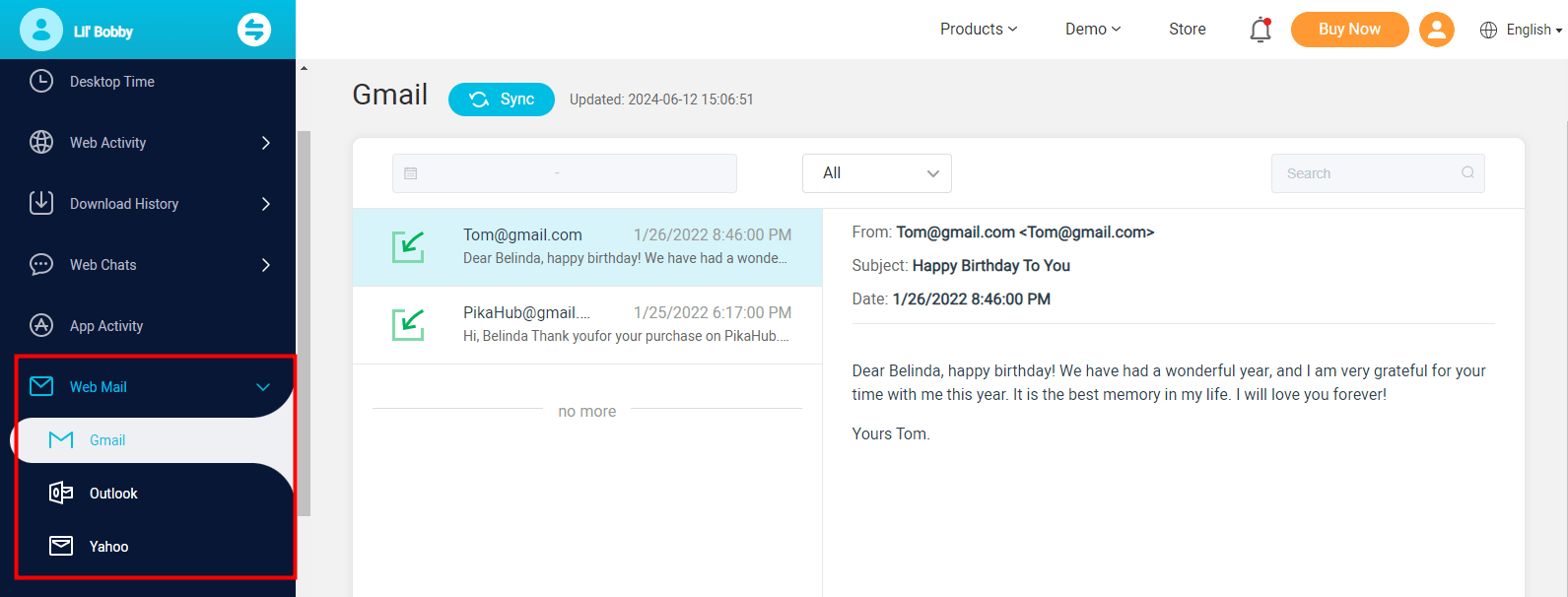
Monitor and read both sent and received emails
All the sent and received emails on Gmail, Yahoo, and Outlook will be monitored. Then, the timestamps, content, contacts, and email subjects will be displayed on the dashboard.
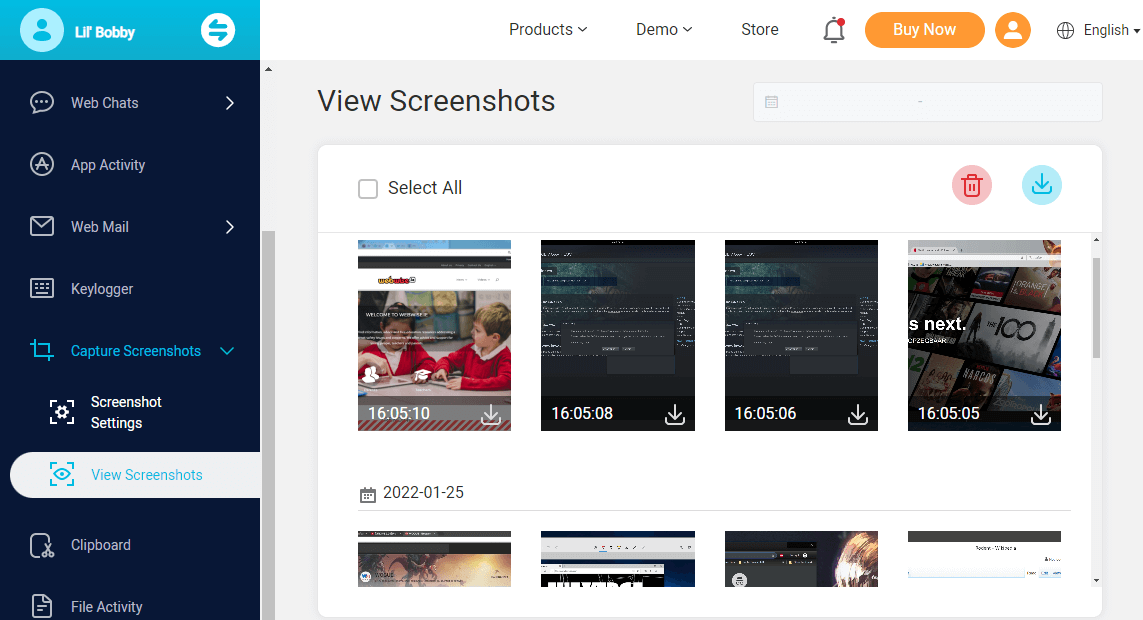
Automatic screenshot of the target computer remotely
The software enables you to capture the screenshot of the target PC every 15 seconds for 5 minutes automatically. It can help you capture the screen in real time so that you can know what the target is doing at that time. All the captured pictures can be downloaded or deleted according to your needs. The screen capture will not send any notifications to the target user.
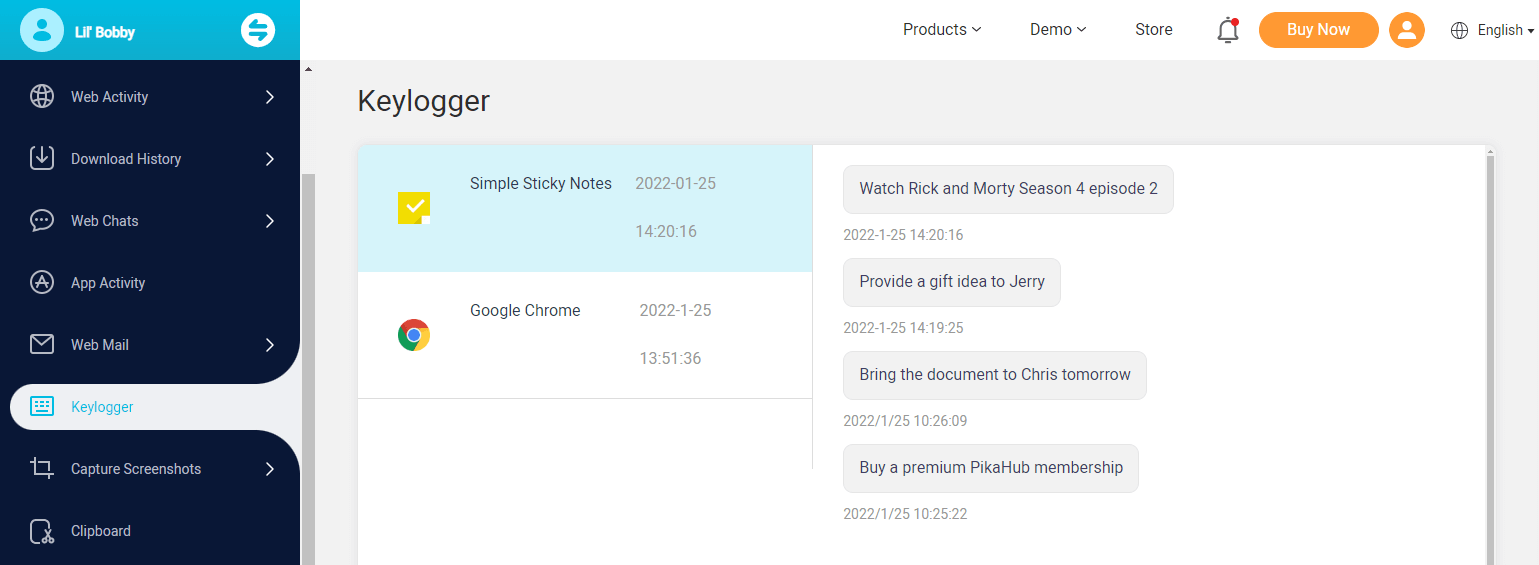
Keystrokes recording
Equipped with a keylogger for Windows, all the keystrokes can be recorded with 100% accuracy. And all the keyboard recording history can be exported to your local computer.
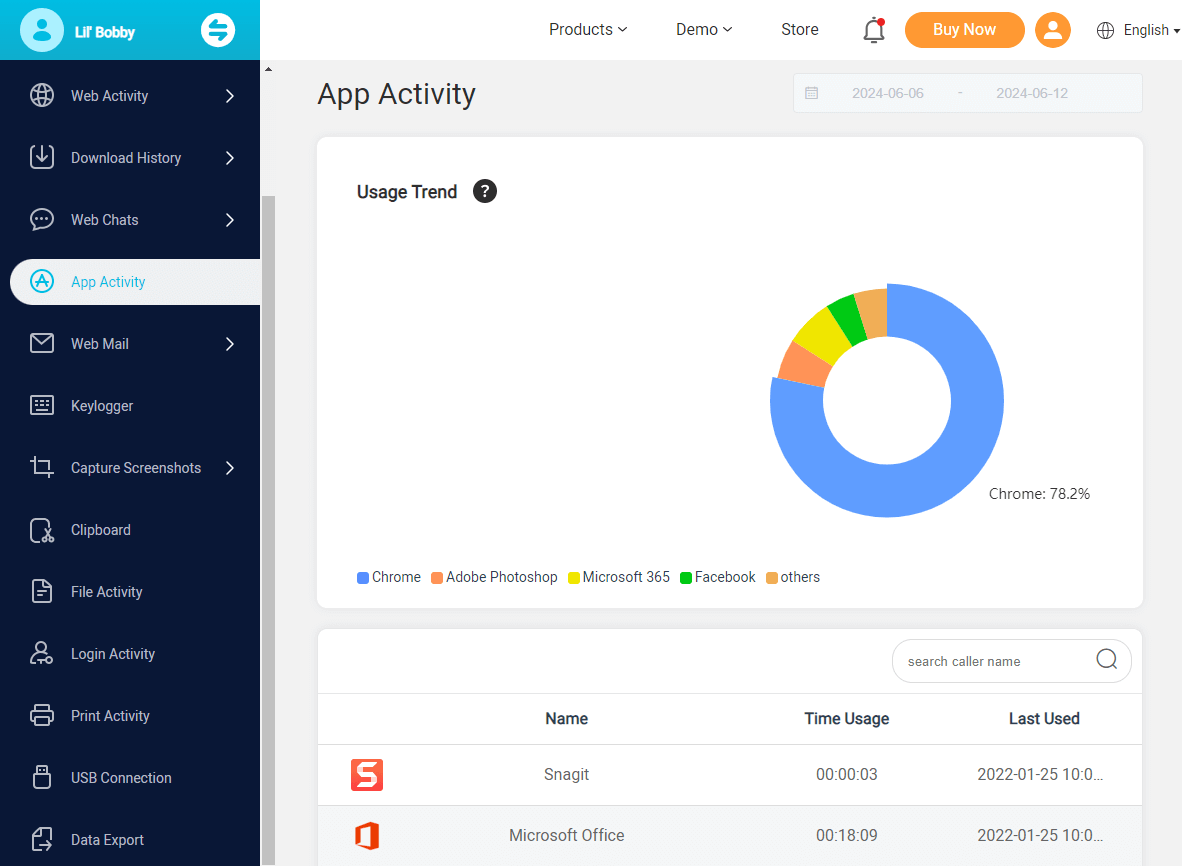
App activity tracker
Track all the software usages on the target computer. It records the app name, the total usage time, and the accurate time.
Login activity monitoring
Time-stamp and log each Windows login activity. You can just tell when the target is online or offline according to this information.
Printing activity monitoring
Every print command carried out on the computer will be tracked. It can tell you which file has been printed and show you the file path. This can be good for monitoring your employees.
Final Words
By now, you already know how to hack an IP address. Admittedly, hacking someone with their IP address is not ethical and thus not recommended. However, if you're looking for a safe and legal way to monitor someone's computer, consider using MoniVisor, a safe and reliable PC monitoring tool.No technical skills are needed and you can easily get the hang of a computer's activity. Don't hesitate to check out the online demo and experience the features first!






