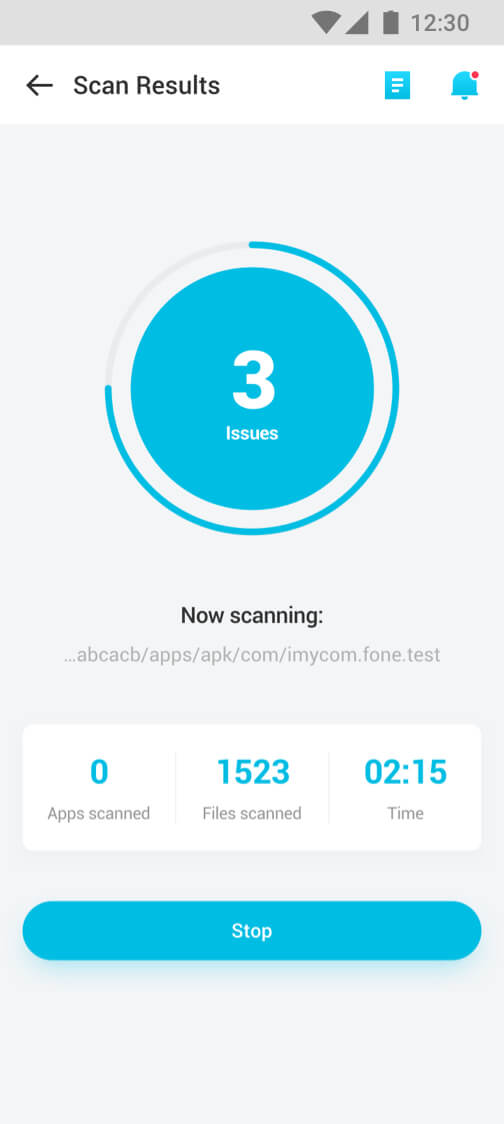
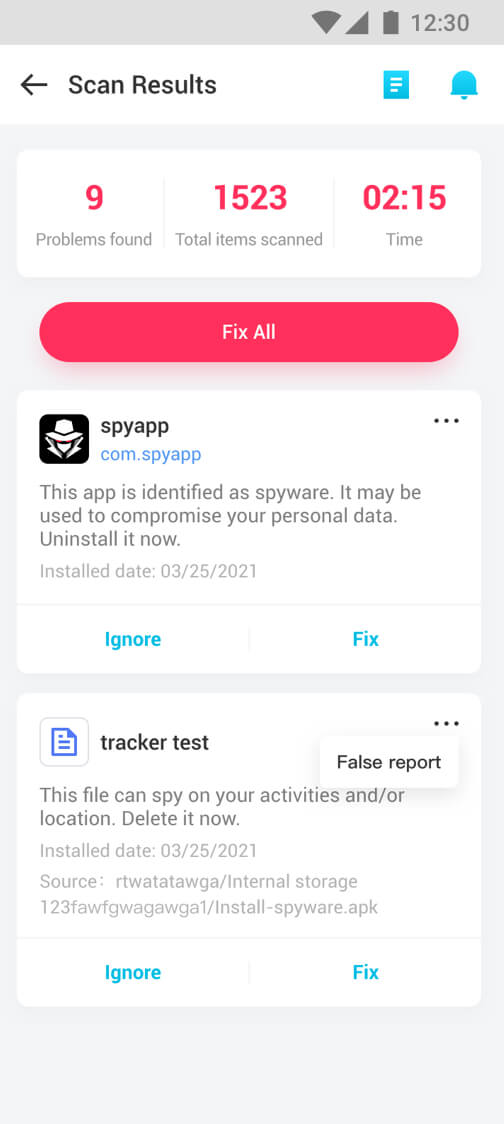
Real-Time Spyware Detector and Remover
- 24/7 heuristic scanning to detect more spyware and trackers.
- Detect and notify malicious files and unsecure apps in real-time.
- Highlight the abnormal records and support removing them all with one click.
- Unlimited and customized Whitelist or Blacklist updates.






Microphone and Camera Protection
- Notify you when any applications turn on microphone or camera with or without your consent.
- Detailed reports on the use of the microphone and camera, including app info, duration, time and date, etc.
- Detect all attempts to access the microphone and camera to prevent unknown attacks.





Detect and Show Hidden App
- Find hidden or suspicious apps which are disguised with fake icons/names.
- Remove all invisible threats going around on your devices.
- Reinforce the security of your mobile against the various risks which can reach you.
- Easily know if WhatsApp is monitored, find GPS tracker on your phone, etc.






Email Leak Checker
- Check if your email has been exposed in a data breach.
- Protect your sensitive online information from prying eyes.
- Professional tips on how to secure your personal info.






Clear Android Junk Files and Data
- Analyze & remove junk files, residual, cache, ad and more which slow down your phone.
- Only a 1-tap boost can free up more space and speed your phone.
- Find out which apps occupy too much memory.





Anti Spyware Solutions Smarter Than You Know
 Hidden Camera Detector
Hidden Camera Detector
Clevguard makes finding hidden cameras easy and fast. Whether they're in your home, a smoke detector, or an Airbnb, the app helps you spot them quickly. Simply scan, and it detects any nearby devices.
 Fake GPS Location
Fake GPS Location
Fake your phone's GPS location to protect your real one. Anyone trying to track you will only see a false location, making it impossible for them to know where you actually are.
 Screenshot Protection
Screenshot Protection
If any app tries to capture or steal your screen content, this feature blocks it. It keeps you safe by blocking apps from accessing your screenshots without permission.
 Secure Photo Storage App
Secure Photo Storage App
Uploading your photos to this storage app, you ensure that no other apps can access or retrieve your pictures. The extra layer of protection keeps your images safe and private.
More Features

Manage every permission you've granted for all apps.

Send suspicious samples to help us rectify the issues.

Remind you which app is threatening the safety of your phone.

Add your trusted app to whitelist without security remind.

Scan the whole phone within minutes and fix all the issures effectively.

Delete any unsecure app or files in one single click.
How to Use ClevGuard to Protect Your Phone
Using ClevGuard anti-spy app to find the hidden spyware and remove the malicious files with several simple steps. ClevGuard can protect your privacy security well.
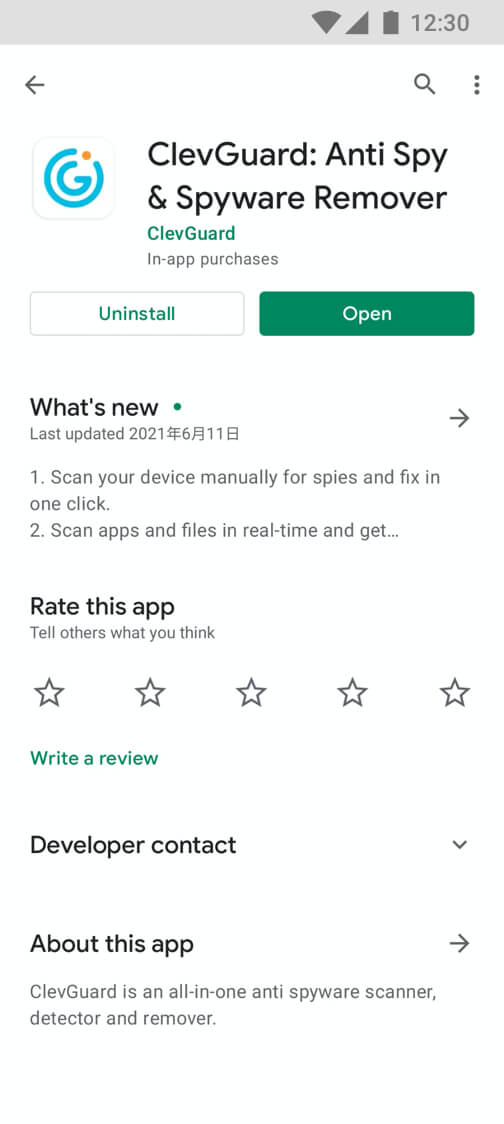
Step 1: Download ClevGuard
Download ClevGuard Spyware Remover on Google Play.
Step 2: ClevGuard Scanner
Scan phone app in real-time and check the result.
Step 3: Remove Spyware
Remove Spyware from phone in few seconds.
Discover Why ClevGuard Is Best Choice
ClevGuard Anti-Spy is one of the best Anti-Spy software for Android and iOS phone users. You will get an overview of why it stands out below.

All in one tool to scan and keep phone away from spying and unsecure state in real time.

You can update whitelist/blacklist database yourself without limitation.

ClevGuard protect phone in real-time. No worry about any spy tool to track your privacy data.

Scan all Third Party app to remind you whether it is safe or not.

We protect every user's data and privacy with high-security standards. Nobody else can access your data.

With user-friendly interface, every user can handle it in several seconds without any trouble.

We provide much cheaper plan for our users to get the best anti-spy software to keep data safe.

Yes, you can upgrade the software and get latest features with no extra cost when updates are available.
Free Version vs Pro Version
ClevGuard Anti Spyware offers 2 different versions. Download for free, and choose whether to upgrade to the Pro version according to your needs.
| Points of Comparison | Free | Pro |
|---|---|---|
| Fast & Full Scan | ||
| Scan Result | ||
| Crush Spyware in One Click | ||
| Real-Time Protection | ||
| Microphone/Camera Abuse Warning | ||
| Email Password Leak Check | ||
| Auto Alert | ||
| App Audit | ||
| Junk Clean | ||
| Unlimited Blocklist & Customized Whitelist | ||
| Enhanced Heuristic Anti-Spy Engine | ||
| Priority Updates of New Signatures | ||
| 24/7 Support | ||
| Buy Now |
FAQs
-
How can I tell if there's a hidden spyware in my phone?
You can use ClevGuard to test if there is a hidden spyware in your phone. Its support detect Application of hazard level determination, Blacklist example monitoring, etc.
-
Where can I download ClevGuard?
You can download it in ClevGuard.com or Google Play.
-
How can I know whether the current version of ClevGuard is the latest one?
You can directly check it’s latest version in our App, if you can’t figure, just contact with our Customer Center for help.
-
Is there any method that can help to prohibit with one-click?
Yes, we support one-click prohibit or open permissions in this App, so you can setting this function and reduce inconvenience caused by operation.
Hot Topics:
- [7 Methods] How Would You Know If Your Phone is Cloned 2023
- [4 Ways] How to Check If Phone Is Rooted
- [2 Ways] How to Hack Android Phone By Sending A Link 2023
- How to Stop Sharing Location Without Them Knowing? - 4 Ways
- [2023] Is Line App Safe? - Truth Revealed!
- Top 6 Anti-Spyware for Android Phones in 2023 [100% work]
- [8 Tips] How to Protect Your Privacy on Kik 2023
- How to Send A Text Message Online from A Fake Number
- 3 Ways to Find out Who Hacked Your Instagram and Solutions