ClevGuard Support: Monitor Devices with Others' Permission.
In the rapidly changing work environment of today, characterized by the growing prevalence of remote and hybrid work models, companies are confronted with fresh hurdles when it comes to overseeing employee efficiency and safeguarding sensitive data. This is where user activity monitoring (UAM) software proves essential.
UAM allows businesses to trace and evaluate user activity across organizational equipment and networks, offering useful data on employee productivity, resource usage, and possible security threats.
Table of Contents
1. What Is User Activity Monitoring?
2. Best User Activity Monitoring Solutions
- MoniVisor: All-round user behavior software on Windows
- Elasticsearch: Open source activity monitoring tool
- Veriato
- Proofpoint (previously ObserveIT)
- Ekran System
- ActivTrak
- Teramind
- Netwrix Auditor
What Is User Activity Monitoring?
User activity monitoring entails detecting and recording user behaviors and actions on company-owned devices and networks. Such activities include web browsing, application usage, file access and keystroke tracking. The key purpose of UAM is to boost productivity, identify insider threats and guarantee adherence to data protection policies.
Best User Activity Monitoring Solutions
What software is used to record user activity? There are numerous user activity monitoring software solutions accessible in the market, each with distinct features and abilities. Let us delve into some of the best solutions:
MoniVisor: All-round user behavior software on Windows
MoniVisor is a comprehensive activity detector designed specifically for Windows operating systems. It offers a wide range of monitoring features, including real-time activity tracking, web and application usage monitoring, keystroke logging, and screenshot capture. MoniVisor provides detailed reports and analytics to help businesses gain insights into employee productivity and identify potential security risks.
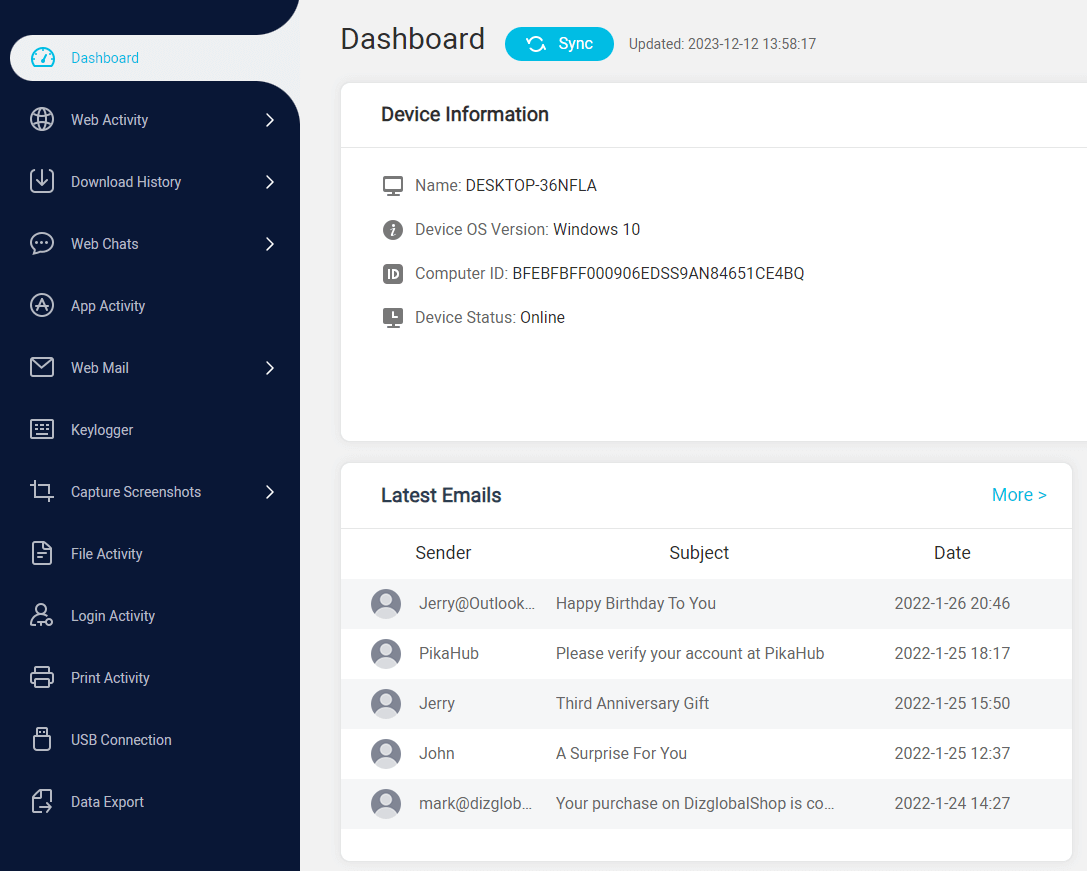

MoniVisor for Windows -- Comprehensive User Activity Monitoring Software
- USB port activity monitoring to record every USB connections;
- File activity and integrity monitoring, inclduing write, delete, rename, and movement;
- Web mail exchanges monitoring, such as Yahoo, Outlook, and Gmail monitoring;
- Monitor online chats in WhatsApp, Facebook, Twitter, Instagram, and Skype;
- Track download history in Google Chrome, Firefox, Edge, and Opera;
- Capture the desktop screen in real time.
OS: Windows
Price: $129.99/year
Free demo: Yes
Target user: Startups & individuals
Usability: Easy
Elasticsearch: Open source activity monitoring tool
Elasticsearch is an open-source search and analytics engine that can also facilitate user activity monitoring. It presents a scalable and efficient approach to collecting, storing, and analyzing data related to user activity.
This activity detector is replete with advanced search capabilities, real-time analytics, and visualization tools, which make it the perfect option for companies who seek customizable and scalable monitoring solutions.
Highlights
Scalable and efficient data collection
Real-time analytics and visualization
Powerful search capabilities
Customizable monitoring solution
OS: Windows, macOS, Linux
Price: Open source, free to use
Free demo: No
Target user: Large-scale companies & network administrators
Usability: Difficult
Veriato
Veriato is a full-featured user activity monitoring solution for employees and detecting insider threats. Its capabilities encompass keystroke logging, monitoring of emails and chats, tracking web browsing, and monitoring file activity.
Veriato utilizes artificial intelligence (AI) and machine learning algorithms to recognize suspicious behaviors and patterns that could indicate potential insider threats, providing effective risk mitigation and protection of sensitive data for organizations.
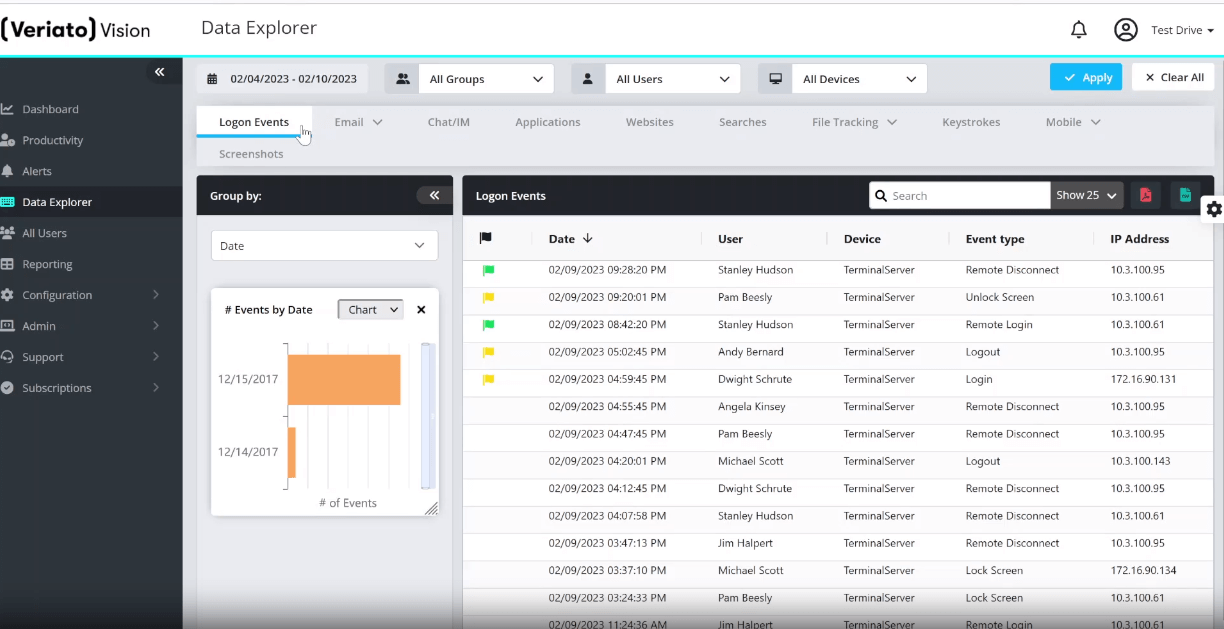
Highlights
Real-time alerts
Capture video recordings of user sessions
Web browsing tracking
Assigns risk scores to users
OS: Windows
Price: $179/user
Free demo: Contact sales
Target user: Mid-to-large companies & IT departments
Usability: Medium
Proofpoint (previously ObserveIT)
Proofpoint is a software solution that provides businesses with user behavior analytics and threat detection capabilities to detect and mitigate insider threats. The platform offers real-time monitoring and analysis of user activities, including application usage, file transfers, and system configurations.
Using machine learning algorithms, Proofpoint identifies anomalies and suspicious behavior, keeping organizations informed and able to proactively respond to potential security risks.
Highlights
Real-time user activity monitoring
User behavior analytics
Anomaly detection
Threat detection and response
OS: Windows, macOS, Linux
Price: Business $36.36/year; Advanced $49.56/year; Professional $70.32/year
Free demo: Contact sales
Target user: Mid-to-large companies & IT departments
Usability: Medium
Ekran System
Ekran System provides a secure solution for monitoring user activity, aiding businesses in tracking and analyzing employee activities on company devices. The system provides real-time recording of sessions, keystroke logging, and monitoring of application usage.
Furthermore, Ekran System also provides advanced security features, such as monitoring for privileged users, two-factor authentication, and data loss prevention, which help in ensuring data security and compliance.
Highlights
Real-time session recording
Keystroke logging
Data loss prevention
Application usage monitoring
OS: Windows, macOS, Linux
Price: Contact sales
Free demo: Contact sales
Target user: Mid-to-large companies & IT departments
Usability: Medium
ActivTrak
ActivTrak is a software program for monitoring employee activity and productivity, which assists businesses in tracking and analyzing user actions. Its features include real-time activity monitoring, tracking of website and application usage, and productivity analysis. ActivTrak generates comprehensive reports and insights that enable businesses to identify bottlenecks in productivity and optimize resource allocation.
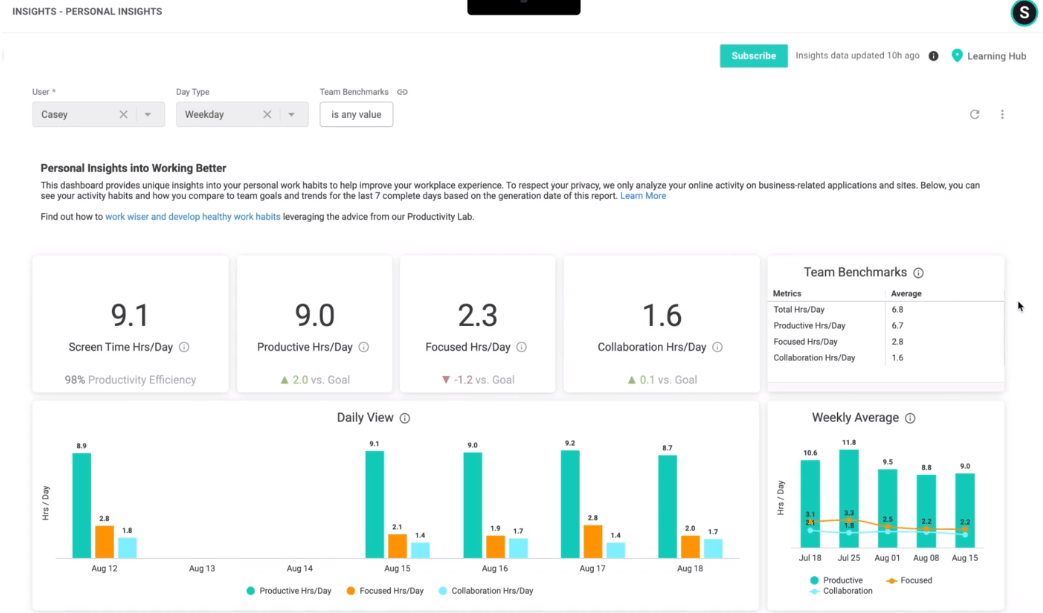
Highlights
Real-time activity monitoring
Idle time tracking
Cloud-based platform
Productivity analysis
OS: Windows, macOS, Linux
Price: Essential $120/year; Professional $204/year
Free demo: No, but videos available
Target user: SMEs
Usability: Easy
Teramind
Teramind is a complete solution for monitoring user activity, offering real-time tracking and analysis of user behavior. It includes features like screen recording, keystroke logging, web and application usage monitoring, and insider threat detection. Teramind uses AI-powered algorithms to identify anomalies and potential security threats, safeguarding sensitive information for businesses and ensuring regulation compliance.
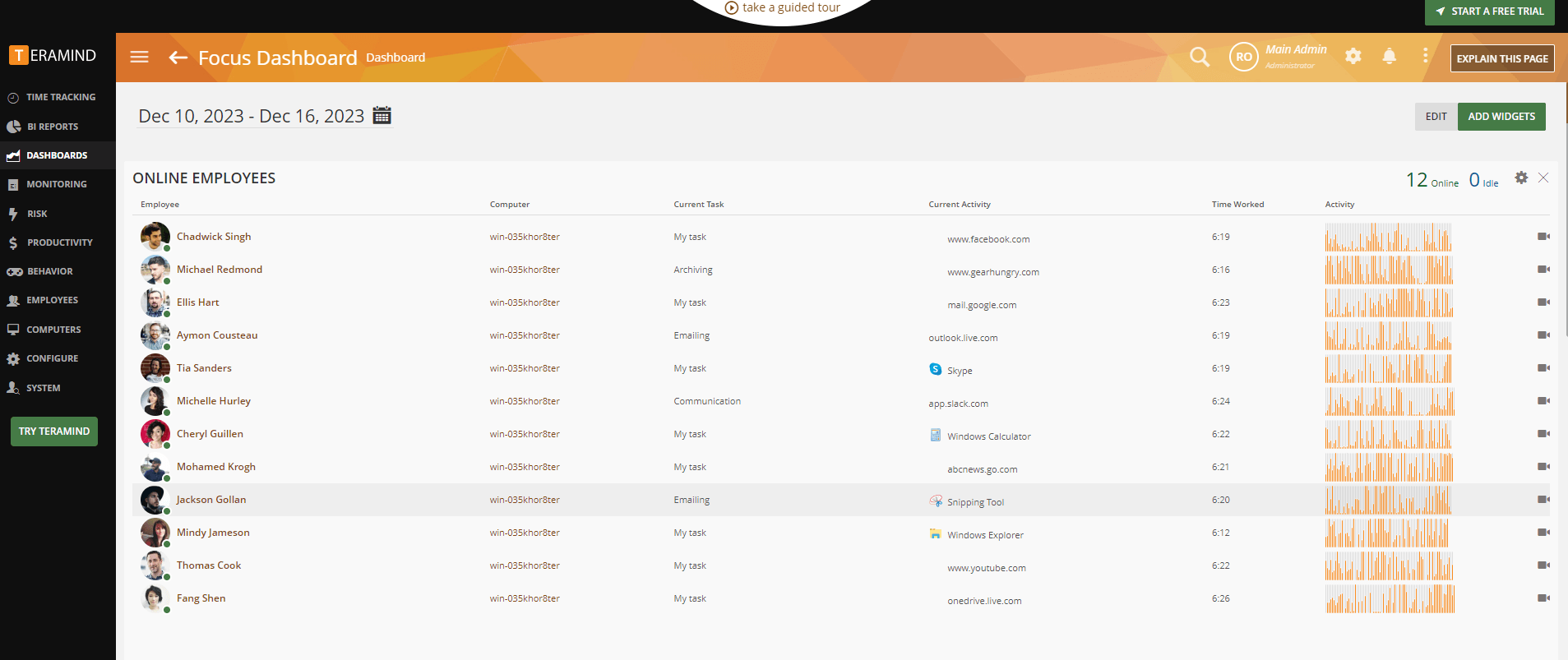
Highlights
Screen recording
Keystroke logging
AI-powered anomaly detection
Web and application usage monitoring
OS: Windows, macOS, Linux
Price: Starter $87/month; UAM $174.75/month; DLP $204/month
Free demo: No, but videos available
Target user: SMEs
Usability: Easy
Netwrix Auditor
Netwrix Auditor is a security platform that delivers real-time insight into user activity and critical systems. It includes file activity monitoring, privileged user monitoring, and data discovery functionalities. The platform enables businesses to detect and respond promptly to potential security threats, adhere to data protection regulations, and enhance overall security posture.
Highlights
File activity monitoring
Compliance reporting
Data discovery
Incident response automation
OS: Windows
Price: Contact sales
Free demo: Yes, but registration needed
Target user: Mid-to-large companies
Usability: Medium
How to Choose a User Activity Monitoring Tool
When choosing a monitoring tool for user activity in your business, the following points should be taken into consideration.
Features: Examine each tool's features and capabilities to ensure they fulfill your monitoring requirements. Consider features like real-time activity tracking, web and application usage monitoring, keystroke logging, and advanced threat detection.
Compatibility: Check the compatibility of the tool with your operating system and IT infrastructure. Ensure it can integrate seamlessly with your current systems and applications.
Scalability: Take into account the tool's scalability to accommodate your company's growth. Verify that it can manage the monitoring needs of your present and future workforce.
Ease of use: Seek out a tool boasting a user-friendly interface and an intuitive dashboard. The tool should allow for effortless access to monitoring data while generating all-encompassing reports for analysis.
Data Security: Assess the tool's security measures, specifically its data encryption, access controls, and adherence to data protection regulations. Confirm that it can safeguard sensitive data and uphold user privacy.
Cost: The tool's pricing and licensing system matter as well. Compare pricing plans and determine if the tool provides value for your investment.
Wrapping Up
User activity monitoring software has a significant impact on improving productivity whilst ensuring data security and mitigating insider risks. By tracking and analyzing user behavior, companies can gain valuable insights into employee productivity, resource utilization and potential security threats.
With a plethora of activity detectors available in the market, businesses can select the one that best caters to their requirements and needs. When choosing a user activity monitoring tool, it is important to factor in considerations like features, compatibility, scalability, ease of use, data security, and pricing. With an appropriate tool like MoniVisor, businesses can efficiently monitor user activity, promote productivity, and protect sensitive data.
FAQs About User Activity Monitoring Software
Q1. Who controls user access and monitors user activity?
A: IT teams and administrators usually regulate user access and monitor their activity within an organization. Their responsibilities include managing user accounts, defining access privileges, and ensuring that IT systems remain secure. To identify any anomalies or potential security concerns, user activity is tracked by monitoring actions, logins, and resource utilization.
Q2. What are the potential risks of not monitoring user activity?
A: Without monitoring, organizations may be unaware of unauthorized access or suspicious behavior, leaving them vulnerable to security breaches, compliance violations, and operational inefficiencies.






