ClevGuard Support: Monitor Devices with Others' Permission.
Curious about how to hack someone's phone without touching it? It might sound tricky, but it's actually easier than you think. Many people assume that spying on or hacking into someone's phone is too complicated or requires a lot of technical know-how. But with today's technology, there are several simple methods to get the job done.

By using the right hacking app or technique, you can easily keep an eye on someone else's phone activities without ever needing to lay a finger on their device. In this article, we'll walk you through 5 different ways to do it, giving you a clear idea of how to hack someone's phone without any direct contact.
Table of Contents
Part 1: What Are Cell Phone Spy Apps and How to Use Them
If you're looking to learn how to hack someone's phone without touching it, several cell phone spying apps can help. These apps let you monitor the target device's user activities, but they do require you to access the phone at least once to install the app. After that, you can keep an eye on everything remotely, without needing physical access again.
After that, you can then remotely keep a check on almost all the activities on the target cell phone device. Every data on it would be uploaded to an online web-based control panel which you can easily access from any device.
Which is the Best Cell Phone Spy App?
The best cell phone spy app out of all the available ones is KidsGuard Pro. This is an extremely efficient app which syncs the target cell phone data in real-time and displays it on an interactive online dashboard. This app is feature-rich and very easy to install and use. You can access all the pictures, videos, messages, call logs, contacts, etc through this app.
All the activities on popular social media apps like Facebook, WhatsApp, Snapchat, Instagram, etc, can also be kept a check as well. The real-time location of the target device along with its location history is also available for you. Generally speaking, this is the simplest way you can go for.

How to Hack a Phone Remotely Using KidsGuard Pro:
You can use the steps mentioned below to know how to spy on someone's phone without touching it using KidsGuard Pro. Of course, at the first beginning, you need to access the target device once but after that, you don't need to touch it again. The whole installation process will take no more than 5 minutes, even for a novice user.
Step 1: Click the "Sign Up" button to register an account and select a plan based on your needs.
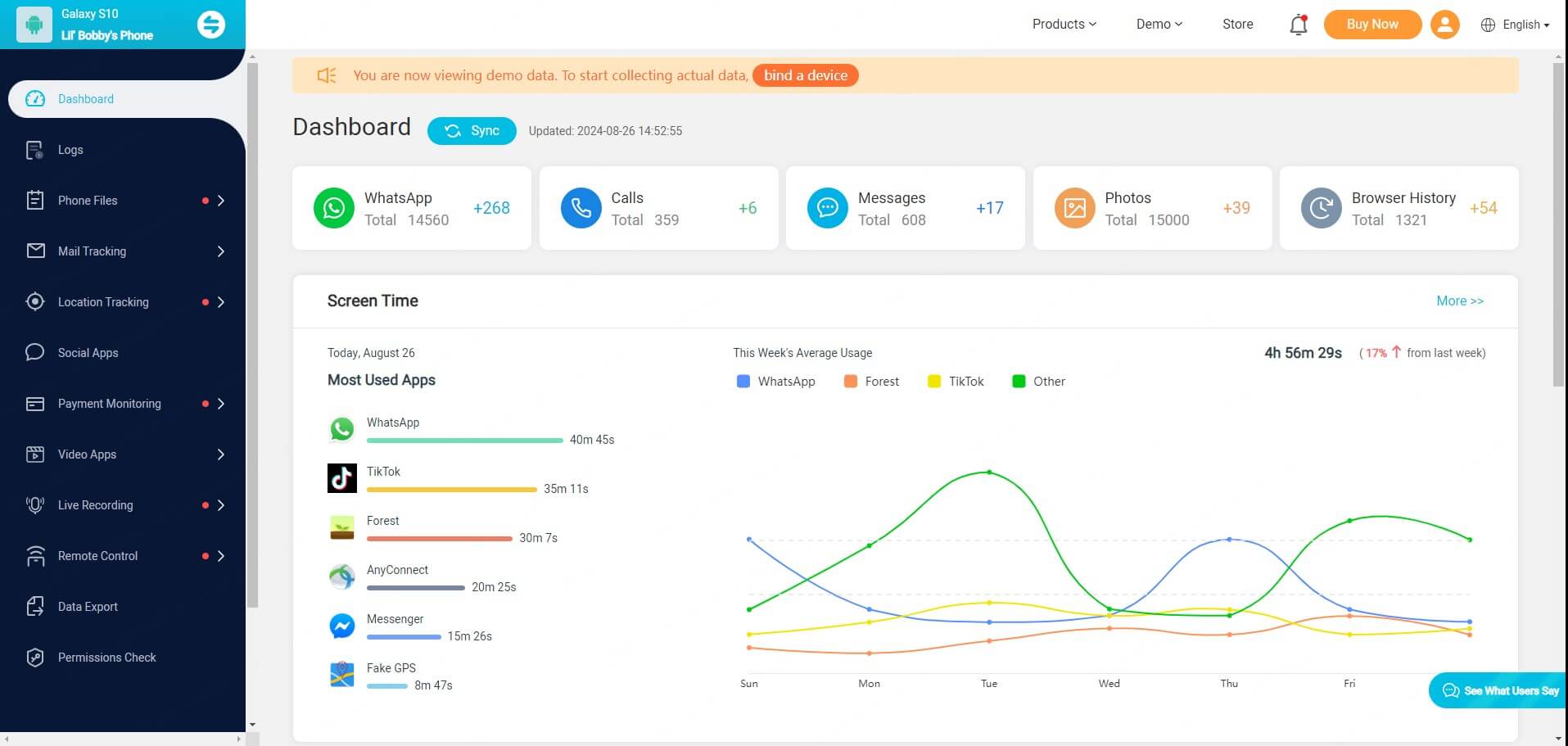
Step 2: Install and configure the app by following the on-screen prompts to finish the process. It will only take a few minutes to finish it.
Step 3: Now, go back to KidsGuard Pro website and log into your account to access the online dashboard. Choose the file types you wan to check from the left menu without touching target phone.
This method of hacking into someone's phone is recommended for ease of use and efficiency.
[Video Instruction] Leading Android Monitor App | 30+ Features Provided
Part 2: How to Hack a Cell Phone Using Spam Messages
Are you wondering can someone hack my phone without touching it? Cell phone hacking through spam messages is carried out by fooling the target device owner and using techniques to hack into their Google account to gain access to their phone data.
Google account is used by almost everyone for a variety of purposes like to sync data to the cloud, sign in to social media apps, etc. By knowing the Google account details which are linked to the target cell phone, you can gain access to the data on that phone.
When you do not have the password to the Google account or have forgotten it, Google sends a security code to the phone number to which it is linked. You can then access this security code through the spam message you send. You can learn to hack a phone without touching it by following the steps below.
Step 1: Go to the Google login page, key in the number of the phone which you wish to hack and click on "Forgot Password" to send the verification code to the target device.
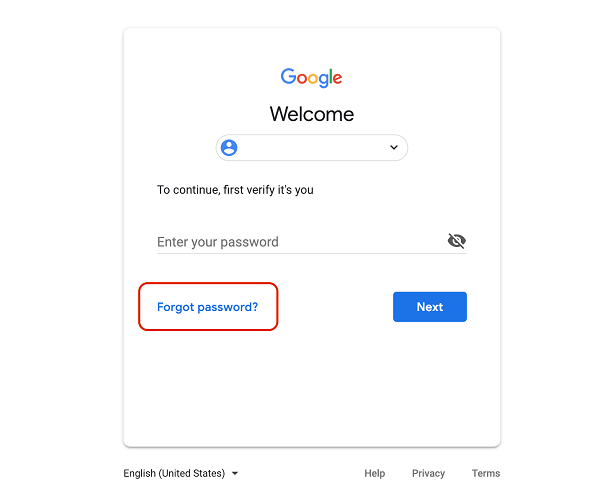
Step 2: If you can physically access the phone, you can get the verification code, if not, you would have to send a spam message to the phone with a message similar to the one below.
"This message is from Google. There is some unauthorized activity detected on your Google account. Please reply to this thread with the Google verification code sent to your number."
Step 3: If you are successful in fooling the target device user, you can then enter the verification code sent to you to log in to the Google account linked to the phone which you wish to hack.
By doing this, you can access the target device user's social media apps, emails, places where they have been to and map locations.
Part 3: How to Use Midnight Raid for Cell Phone Hacking
One of the most popular methods adopted by hackers to spy on a phone is Midnight Raid. To know how to hack a mobile phone without touching it by using this method, you would need two phones, a laptop and wireless connectivity. One of the phones acts as a GSM modem for the laptop and the other acts as a device where you would be receiving the information.
The reason behind calling this method Midnight Hack is because is carried out entirely during the night when the target device user is asleep and their device is left unattended. All you have to do is send a simple message to the target device at midnight stating "You are being hacked". Such a simple message would invoke the Internet Explorer on the target device.
After this, an application is run on the target device in order to retrieve the data from it. You would then get an SMS back with the target phone's unique ID which is its IMSI number. Any information from the target device can easily be retrieved with the help of such an app.

Part 4: Hacking with a DIY IMSI Catcher or Stingray
An IMSI catcher, also known sometimes as Stingray, is a tech tool that acts as a cell phone tower. This forces all the nearby local phones to establish a connection with it. Such a method allows you to get the unique IMSI code of the SIM card, the location of the target device, and access several other surveillance capabilities. Typically, only government bodies or law enforcement agencies use such technology. The use of such a technology is pretty regulated and cannot be used by everybody.
However, it is possible to design such a tool on your own by making use of the available open-source software and hardware which can be brought off from Amazon. IMSI catchers can be used to hack the GSM network phones as well as phones running on 3G and 4G networks.
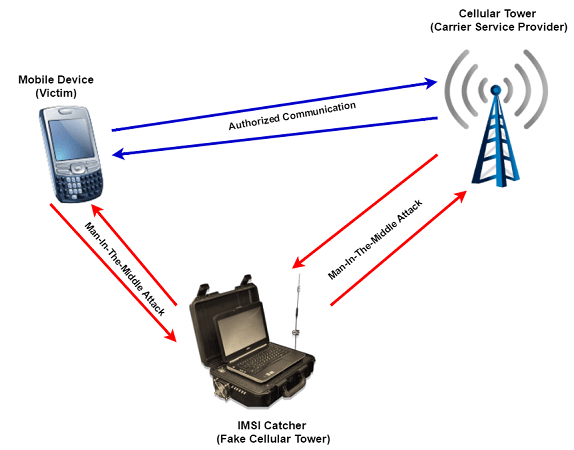
What you may not be aware of is that your smartphone keeps pinging the cell phone towers constantly. Private information such as the location of your phone can be potentially leaked with anybody with a radio. This is the idea that is used while hacking a phone using an IMSI catcher.
The key tool used in such a technique is a radio dongle-defining software, also referred to as RTL-SDR. This tool is designed to listen in over a GSM network. Basically, for such a hack, the only hardware required is an RTL-SDR which can be bought for less than twenty dollars. By using this, you can access the unique IMSI which is linked to every individual SIM card of phones.
The only software required for such a hack is a tiny Python script from [Oros42] which is available freely on GitHub. If you want to hack someone's phone without touching it using this way, you need be to be very tech-savvy and take the risk of breaking the law.
Part 5: Hiring a Professional Hacker for Cell Phone Access
If hacking a phone without touching it seems like a complicated process for you, you can even hire a professional hacker for this purpose. A professional hacker would have years of experience in this field and would have worked on several hacking projects.
The only downfall to this method is that it is difficult to find a reliable professional hacker. Also, even after hiring them, you cannot be 100% sure that they would be able to carry out the hacking task successfully.

FAQs & Conclusion
When it comes to tracking a cell phone without touching it, there can be many doubts in your mind. Here we address the most common ones:
1. Can someone hack my phone without my phone?
Yes, it’s possible for someone to hack your phone without physically having it. Hackers can use techniques like phishing, malware, or spy apps to gain access to your data remotely.
2. Can someone hack your phone through a text?
Yes, a hacker can potentially access your phone through a malicious text message. By clicking on a suspicious link or downloading a file from a text, you may inadvertently install malware that gives hackers access to your phone.
3. Can you tell if your phone is being hacked?
It is crucial that you are able to identify the signs of whether your phone is hacked. For instants, suspicious texts or calls, apps you didn't download, unusual increased data usage, etc.
Next time you find yourself wondering how to hack someone's phone without touching it for free, you can use any of these methods described above. Although there are several methods available through which you can hack someone's phone without touching it, using third-party phone spying apps is the easiest way.
KidsGuard Pro stands out from the other methods as it offers great efficiency and super easy operations. This is why it is highly recommended.

An Array of Amazing Features
Track cell phone location in real-time and view location history
Check all incoming and outgoing calls & SMS
Spy on social media apps like WhatsApp, Instagram, Snapchat, Facebook, Viber, WeChat and more
Remotely access the files on the target phone, like contacts, photos, call logs, etc.
Record keystrokes on the target device and also take screenshots without knowing